Industrial Cybersecurity for Intelligent Operations
Protecting industrial control systems, operations, and data from evolving cyber threats with SUPCON's multi-layered defense approach.
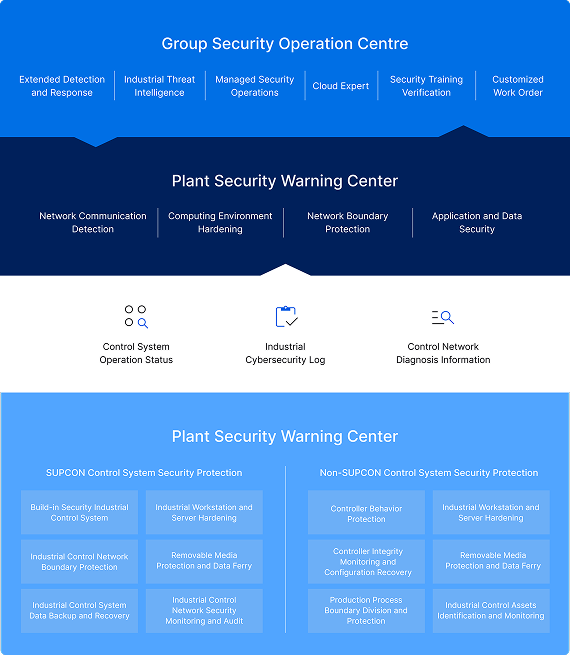
Securing Industrial Intelligence with SUPCON's 1+1+2 Cybersecurity Operation Solution
As the connectivity between IT and OT systems is increasing, industrial operations face escalating cyber threats. SUPCON’s 1+1+2 Cybersecurity Operation Solution delivers layered protection—from group-level security operation to field-level security management—ensuring secure, intelligent operations.
Cybersecurity Product Solutions
Modular Security Building Blocks for Industrial Cybersecurity
SUPCON provides a suite of targeted cybersecurity products engineered for industrial control environments. Each solution is designed to address a specific layer of defense—from endpoint protection to asset management—enabling a secure-by-design approach for smart manufacturing.

NG USB Guard
Controls portable device access. Prevents malware intrusion with antivirus scanning and audit logging.

RTU Secure
Prevents unauthorized access at remote or unmanned stations with multi-factor authentication and video surveillance.

Industrial Firewall
In-depth inspection of industrial control protocols with fine-grained access control.
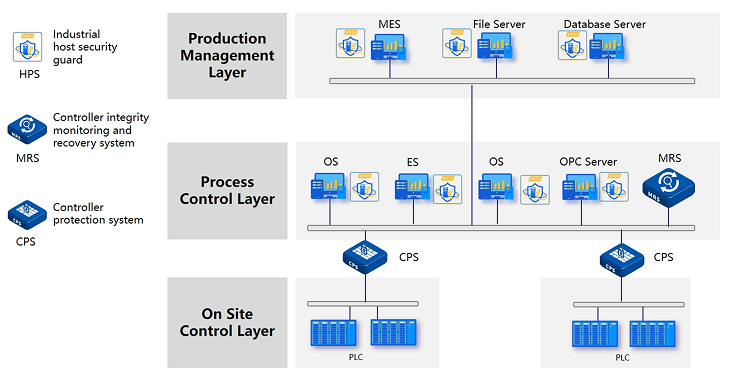
Security Shield for Control System
Protects control systems at the controller and host level. Blocks unauthorized operations and supports program recovery.

Industrial Control Asset Health Monitoring System
Monitors industrial network status in real time. Auto-discovers asset topology and detects anomalies.
Cybersecurity Product Solutions
Modular Security Building Blocks for Industrial Cybersecurity
SUPCON provides a suite of targeted cybersecurity products engineered for industrial control environments. Each solution is designed to address a specific layer of defense—from endpoint protection to asset management—enabling a secure-by-design approach for smart manufacturing.

NG USB Guard
Controls portable device access. Prevents malware intrusion with antivirus scanning and audit logging.

RTU Secure
Prevents unauthorized access at remote or unmanned stations with multi-factor authentication and video surveillance.

Industrial Firewall
In-depth inspection of industrial control protocols with fine-grained access control.

Security Shield for Control System
Protects control systems at the controller and host level. Blocks unauthorized operations and supports program recovery.

Industrial Control Asset Health Monitoring System
Monitors industrial network status in real time. Auto-discovers asset topology and detects anomalies.
Scenario-Based Protection
Cybersecurity Solutions for Real-World Industrial Threats
From host vulnerabilities to remote physical intrusion, SUPCON provides targeted security strategies that match practical industrial use cases. Our approach is not theoretical—it is deployed, tested, and trusted in complex OT/IT environments.
Shields industrial controllers against logic tampering unauthorized operations, and malware. Enables program backup and fast recovery.
Protects industrial hosts via allowlisting, OS/AV patch management, USB flash drive control, and virus detection, etc. in stable, continuous-use environments.
Industrial firewalls provide deep packet inspection of multiple industrial control protocols and prevent tag tampering, forged packets, unauthorized operations.
Controls portable device access, identifies encrypted files, quarantines unknown files, and prevents infection via removable storage devices.
Prevents unauthorized access and physical intrusion at unmanned distributed stations via Zero Trust authentication, RTU isolation, and camera surveillance.
Enables real-time network visualization, monitors controller/switch/workstation/firewall health, detects anomalies of network and devices.
Certifications & Compliance
Built to Meet Global Industrial Cybersecurity Standards
SUPCON's cybersecurity solutions are not only battle-tested in industrial environments—they are also backed by rigorous international and industry-specific certifications. Our commitment to security governance, system resilience, and lifecycle operations ensures that we meet and exceed compliance expectations across global markets.
Product development and protection strategies align with global industrial cybersecurity standard IEC62443.
SUPCON maintains ISO/IEC 27001 certification for information security management across products and services.
Certified by China's Ministry of Public Security for industrial security product compliance and sales licensing.
SUPCON regularly issues security bulletins and threat advisories in alignment with global vulnerability reporting practices.
Our Product Security Incident Response Team (PSIRT) coordinates vulnerability management and incident response globally.
SUPCON operates internal training programs and cyber range facilities to support secure development and field response readiness.

Enhancing Remote Site Security with RTU Secure

Deployed RTU Secure at remote Aramco sites to reinforce physical and network security. Enabled real-time monitoring, access control, and secure operations in challenging field environments.

